Hello all!
Today will be yet another post without code (yet without enough time), but showing you what I think are some big security faults I found in a very popular site, hackerrank. This is a site where one can attempt solving from very easy computer programming problems, to very big ones where are implied performance in time and resources. As well, attempts to teach the most known algorithms and got very interesting contests, and job offers as well. Here below, for example, one of sudoku golf, where challenge was to solve, in a very limited time, a very big number of sudokus (I think there was more than 1000000, dont remember), and, as well, with codegolf conditions: with the minimum number of chars in source code. I’m proud of myself having reached a 82.73 over 100 score, using a non-functional language as is pure C (was second position in my country 🙂

This site got, as well, interesting exercises about Linux Bash. I begin to realize the exercises, that are realized in what I though at first as a virtual bash interpreter. Exercises where easy (grep, awk, etc…) and then I attempt to just do another thing, by curiosity, just an ls. My surprise was that got access to running files in what seems a home dir: solution.sh was the script I sent from web page, input was input send to that code, request.json was the arrived json from my request, etc…

Ops! so there’s something like a real Linux, not just a bash interpreter. I begin more ambitious and search from root dir…And yes! it gives me info about everything!

I continue then checking out ifconfig, netstat, lshw, lspci, … and all of that commands gives to me info…It says to me that was an ubuntu, and seems not running in a virtual machine, so real servers (or cloud ones). Deducted that although seems a full linux machine, not just a bash interpreter, seems that there was dynamic Ip allocation & different network conditions at each session call. Checking more over, I see that MAC Address for ethernet card was changing all the time, and as well, internal Ip assignment (resolv.conf but remain the same), and internal open connections (although some of the external connected Ips seems the same to me sometimes). So, I think that I am accessing into ephimeral Linux machines in a cloud service as can be Azure or AWS, presumably an Azure, due the hardware info gives to me lshw (all Intel hardware)

So, I dont found any relation between each session call or another. As well, although $USER variable gives nothing to me, or whoiam command , I found that my user was execute-user-<number>, automatically assigned from site session, and that got assigned a running dir at root, and of course, that at each session call my user changes…I attempt to persist files, just echoing, and although files persist in each call, there was not persisting between them. So, anything done should be did just in a session call…for example, get /etc/passwd…

Or resolv.conf…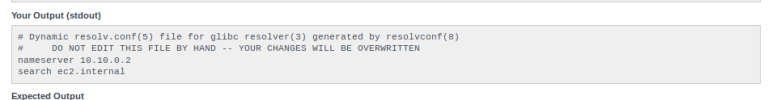
I didnt found shadow file (with hashed users passwords), surely its hidden or got remote password check, but anyway all this gives me options to find a real hole (as always, with enough time and job ).
Inspecting, I found another gem: there was a keystore at /etc

Keystore files are java files to store private keys, ssl certificates, etc. SSL certificates and so on, are a way to ensure identity of an user: for example, a site can ensure it’s the site it says if its exposed SSL certificate, validated by a trusted entity (GoDaddy, for example) says that is that site: it’s a way to avoid phishing. As well, can be used for clients and be verified by server, denying each client request that was not recognized by server.As well, SSL Keys & certificates are used to allow ssh sessions without authentication, or for example as same by its name in this case, to sign an application and upload it to Google Play. In general, SSL certificates are used to certificate identity. Internally, keystores can save whole files needed for ensuring it: the trusting entity certificate, the trusted site/application certificate itself, and a private key. Private key uses to be a sha hash (sha2 512 the most of the time) that is combined at the moment of generating the ssl certificate, acting as a glue or as a catalyzer, with the entity certificate and the site/app one, making a relation between them. In another words: it’s the part that ensures that the certificate for my site is trusted by the trusting entity. As well, this private key it’s needed to use that certificates. So, if I got the certificates but not the key, cannot do nothing…but If I got it, I can use whole certificates to, for example, simulate without no risk another web page…In fact, private keys are used to be stored very privately : are the main point to all other identity security.
So, I get this one…

In our case, I get it and save it to my local computer, decoding again using base64 -d . Then I use keytool to check what was inside the repository… It ask a general password to me…I attempt without no one…and works!
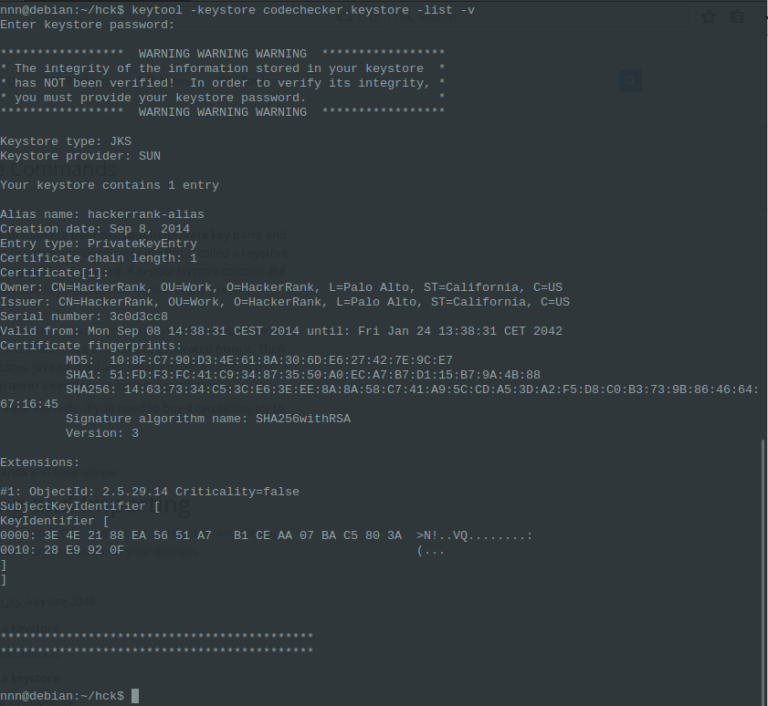
Seems that there was a certificate private key, and seems a lot that was used, by its name, to sign an android app (at release phase) or a site. Perhaps was deprecated, perhaps was useless, but anyway, seems interesting to me.
To extract and to use that private key from keystore, I need a password…that unfortunallety I dont got.

But, now, I can crack it without any external intromission. In fact, that situation is the same as one with a closed safebox at home, attempting to open it with time and no pression.
To crack passwords, there’s a lot of utilities… I found this one that gets a hash valid for Kali Linux hashcat,

which is a brute-force (with another cracking methods) tool for cracking hashes, and where you can set up guessed mask, length, an a lot of variables to approach faster to results. Anyway, brute-force attack can last a lot of days…and that’s where I am right now 🙂

As told, It is very possible that when hashcat find the password, I find that private key is really useless to me. Can be, as well, that people in hackerrank knows that is accessible just by its site web terminal, and let it there conciously. As well, I’m not going at first attempt to do nothing with this, just exposing some of the what I think are big security failures (from firewall):
- First: if you’re using cloud/real linux machines (not just bash interpreters) then should be a good policy to make that external users, the ones automatically used, with the few permissions possible. In fact, can be added to a group and that group to be banned to all except their tasks. Ban to do anything is ban to read files, to enter dirs, etc…In fact right now I see that is possible to rewrite some files, i.e., /etc/passwd, just using sed and changing /sbin/nologin to /bin/bash, so, allowing an execute-user-<n> to enter in a real bash session…
- Second: not let security keys accessible and with a so clear name (codechecker-android-release-key.keystore). It is very possible that this key is useless: take in care that hackerrank it’s, in fact, just a big programming sandbox). But anyway, I think it’s not the way to store them.
- Not let keystore without a general password…
- To not allow any user to use system commands as netstat, ifconfig, lshw, lspci, etc…although perhaps your system seems protected, with system commands you can analyze and, perhaps, found something you had passed out. Netstat let me show what is seen in network from inside, to see which connections got open, and so, which ips are accesible from that machine, and which ports, etc…I think anyway that is the default behavior in ubuntu, making Linux easier. So, perhaps using another distro could be a fast solution…
- It’s a general fault to left the most of the security to firewall/IT. This example shows that, although firewall can block and filter a lot, every part should be checked, and not to put all security duty to principal entering gate.
- And so on…
I think that if it has not been left conciously, this is provoqued because designers applied just ‘academical’ solutions, I mean, without thinking that it was possible to anybody not to attempt the exercise but anything else, without suspecting the possible curiosity that can got anyone…
Anything else! If I got more results (i.e, ssh root access to full hackerrank network ) will notice you about 🙂
Best,

I think you are wrong, all you describe indicates that the command runs in a virtual machine that is created only for and during execution of the command. So you are in a sandbox, and whatever you do will have no effect. Also, you won’t be able to get any interesting passwords because you are the only user on that virtual machine. There’s no issue if you gain root access and delete the entire file system, because it will disappear anyway once your command is done. And I’m quite confident that you cannot go anywhere outside that virtual machine.
LikeLike
Yes, they’re sandboxs. In fact, I named them in article as ‘ephimeral Linux machines’ to reach a maximum of readers. Perhaps not so much verbose and understable… Anyway, real fact was that SSL certificate is a real one, signed, with CN=HackerRank, and its a private key, so obtaining it and obtaining public ssl certificate from web or app, could give someone possibility of phishing hackerrank in web or some app, without too much effort. Article itself is just an example.
Anyway, I should review & improve all articles, and launch again examples. A pity, but not enough time…
Thanks for your comments!
LikeLike